SASE, a cyber security solution, is an integral part of the security of distributed information systems. The evolving security strategy recognizes the prevalence of distributed information systems in today’s modern work patterns.
The users working in companies increasingly prefer secure corporate data center-based cloud services. SASE solutions enable end-to-end security for the distributed data centers across the system infrastructure. Before exploring the future of network security, let’s understand the different aspects of SASE.
Understanding SASE
SASE has built-in threat-prevention features for network security like firewalls, URL filtering, anti-malware, and intrusion-prevention systems, These features encrypt all communications to ensure secure internet access and prevent data loss.
All globally connected network edges have access to these network security functions. In this article, we are going to discover the application, future, and potential of SASE solutions.
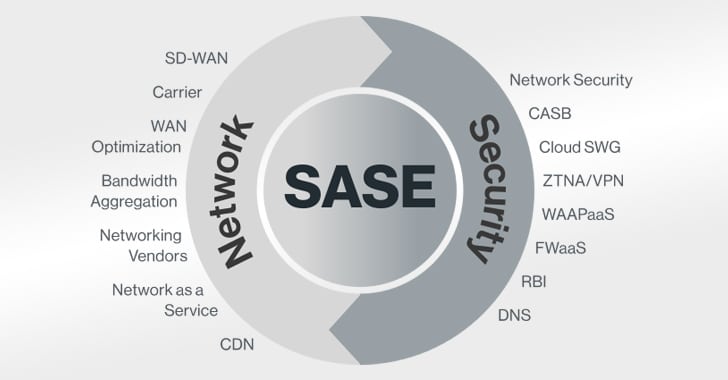
Core Components of a SASE Architecture
The network and security tools used in the SASE architecture’s implementation across an organization’s IT infrastructure are essentially a set of various tools of security. SASE can be broken down into six main components in terms of its features and technologies, whether they are essential components that make up the network perimeter of SASE.
Three main structural units make up the comprehensive system design security network infrastructure known as SASE, which works as a whole to provide maximum security. Additionally, they do away with the necessity of inspection engines in data centers. Included in these three sub-architectures are:
- Cloud Security Services
- ZTNA
- Network Services
1. Cloud Security
The following are components of this type of security:
Firewall as a Service, or FWaaS
Limiting access, advanced threat prevention, URL filtering, DNS filtering, intrusion prevention systems, and DNS security are all features of cloud infrastructure. You can use these services in place of actual firewall hardware, thanks to the firewall services.
Secure Web Gateway (SWG)
SWGs, or secure web gateways, prevent unauthorized external devices from accessing your internal network. It shields your employees and clients from online dangers like malicious traffic, unsafe websites, viruses, malware, and phishing scams.
Cloud Access Security Broker (CASB)
The use of CASBs prevents data leaks, malware attacks, regulatory non-compliance, and lack of visibility by ensuring secure cloud applications and service usage. They safeguard cloud applications whether they are hosted in a private cloud, public cloud (IaaS), or SaaS.
2. ZTNA, or Zero Trust Network Access
Thanks to ZTNA’s technologies and services, the enterprise software can be used securely off-premises. The least-privileged access is always permitted under predetermined rules in a zero-trust framework.
SDP
The outermost SASE layer, known as the Software-Defined Perimeter (SDP), is made up of all the networking and security tools required to securely connect the core entities. The SDP follows the fluid relationships between crucial entities rather than the rigid boundaries of conventional network architectures, which are based on fixed locations, geography, physical network zones, IP addressing, or buildings.
3. Network Services
A company’s wide area network (WAN) is protected by SASE, which is also designed to increase the effectiveness of its decentralized networks. This is accomplished by integrating the capabilities of a software-defined wide-area network (SD-WAN) and securing transient and mobile users through a secure web gateway.
SD-WAN
SD-WAN is a “wide area network,” providing a software-defined security service edge. The most direct path for an organization’s data to and from the cloud, on-premises applications, and the rest of the network can be achieved with software-defined wide area networking (SD-WAN).
How SASE Addresses Modern Cybersecurity Threats
Effective SASE deployments create a centralized management approach to security by leveraging a variety of tools and capabilities. The organization’s data and security infrastructure are shielded from a variety of security threats due to the combination of numerous different security services and capabilities that are delivered to endpoint devices through the cloud access service edge.
SASE delivers consistent, adaptable security services, including threat prevention and NGFW policies, a secure web gateway, and ensuring zero-trust network access. In this way, you can fill the security gaps and know who is on your corporate network, what is on it, and how to protect assets both on and off the network.
SASE and Remote Work
By moving the point of security policy enforcement away from the corporate network and applying secure remote access service edge wherever remote workers are located, SASE technology enables remote work and the use of cloud-based services.
Regardless of their physical location or network connectivity, end-user devices and other security tools consistently comprehend and apply the organization’s security policies. Knowing that remote users are subject to the same security requirements as those who use devices on corporate networks allows technology teams to rest easy at night.
Comparing SASE with Traditional Network Security Approaches
Comparing SASE to conventional network security solutions is a divergence in favor of a more thorough and flexible strategy. This strategy combines various network and security functions into a single framework, improving visibility, data protection, access control, and threat adaptability.
In traditional network security solutions, various security functions are typically implemented in layers as part of a security stack. This strategy frequently results in complexity, inefficiency, and higher management costs.
Zero Trust and SASE
ZTNA is the cornerstone of SDP. Every access request must undergo identity and context-based authentication as part of the Zero Trust Network Access (ZTNA) guiding principle. ZTNA is in charge of user authentication to apps within a SASE architecture by utilizing sophisticated context and role-based identities in conjunction with Multi-factor Authentication (MFA).
Predictions for SASE’s Evolution in the Coming Decade
As more businesses adopt cloud and remote work models, SASE is anticipated to provide consistent security and expand quickly over the next ten years.
According to SASE Forecast Analysis, this cloud-based security framework will take over as the standard enterprise networking and security architecture. The global market for SASE is anticipated to reach $15 billion in value by 2025, growing at a remarkable CAGR of 36% since 2021. Up from less than 1% in 2018, at least 40% of enterprises will have explicit strategies and timelines for SASE adoption by 2024.
Enterprise networks will be able to scale up or down security services using SASE without sacrificing user experience or performance.
SASE will make use of artificial intelligence and machine learning to enhance network traffic, performance, and efficiency, as well as to detect and respond to threats in real time.