What is Role- Based Access Control?.. Organizations of all sizes care about securing their IT investments, and a key part of that is giving users limited access to only the resources they need to do their jobs. This can be introduce as the principle of least privilege in Role Based Access Control.
While this is a laudable goal, it has often been too long and complicated to implement effectively. As more data and systems are connects each year it’s faster to deploy. Therefore a simpler way to manage access is essential. That’s where role-based access control (RBAC) comes in.
- What is Role Based Access Control?
- How is Role Based Access Control helpful?
- Best Practices for RBAC Implementations
- Azure Role Based Access Control
What is Role-Base Access Control (RBAC)?
Role-Base Access Control (RBAC) is the modern role-base permissions management model that helps manage access both at a general level and at a granular level by aligning the assign role of permissions with the user’s organizational role. It helps prevent access leaks and thus reduces the risk of data and information security breaches.
As we mention earlier that RBAC is an approach, meaning that it was designed to addition other existing security policies to strengthen the enterprise security landscape. Basically, RBAC provides a way to group different types of permissions across the enterprise and categorize them to assign those permissions efficiently based on user roles.
Groups and Roles – The Difference
A very important point is that there are differences between groups and roles. Groups are use to organize users who have the same level of permissions to perform a task. This may or may not be relevant to your job functions, whereas roles are aligning with job functions and are a group of access privileges to perform a specific job.
Attribute-Based Access Control (ABAC) an alternative to RBAC
According to another viewpoint about user security and permission management is attribute-base access control (ABAC). Hence it seeks to match the characteristics of the user with the resources that the end-user needs to access to perform their tasks.
Up to this point, this system has not gained popularity due to the challenges and configuration required to implement this system on a large scale.
How is Role-Base Access Control Helpful?
Regular audits of permissions and access are essential to maintaining security within an organization. However, manual audits take an excessive amount of time. As a result, if they are not perform as often as they should be. RBAC streamlines audits by apply uniform access across the enterprise.
Other benefits of Role-Based Access Control are:
Compliance
Role-based access control helps organizations meet agreement regulations, such as privacy and data protection directions imposed by regional and local government agencies. Examples include:
- HIPPA compliance for healthcare organizations.
- CCPA for large California organizations.
- GDPR for organizations handling the private information of European Citizens.
Operational Efficiency
Role-based access control helps improve and maximize the operational efficiency of security actions. If access controls are assign using a role-based approach, they can be exchange quickly and consistently across the enterprise.
Increased Visibility
Role-based access control provides more visibility into who has access to what resources, ensuring that resources are only accessible to users authorized to perform assigned tasks.
Reducing Operations Expenses
Role-based access control also helps regulate and reduce operating expenses (OpEx) as it works on the principle of least privilege and reduces IT support and administrative staff from manually managing access permissions . Now they can spend their time on more productive work tasks.
Best Practices for RBAC Implementations
Implementing RBAC requires organizations to spend time thinking about how their internal processes work and designing roles that align with user roles.
What follows are the necessary methods to start doing this within your organization:
1.Inventory systems and software– List all corporate resources a user might need access to, including applications, software, hardware, and any other intelligently managed resources (using smart maps, etc.)
2.Identify and list required roles – Analyse current user permissions and based on that, create roles. It may be helpful to ask your help desk to compile a report. And also on access requests from which you can find usage patterns. Note that you should create high-level roles. Hence too many micro-level roles can completely defeat the purpose of going through the role-based access control process. There may also be common groups, where all resources are map and have similar access levels, such as: email groups, print user groups, Internet groups, etc.
3.Assign roles to resources – Once the roles are create, assign the roles to the resources for proper access management and resource visibility.
4.Assign users to roles – Assign the group of users with similar access levels to the newly created roles. Since these roles are already assigned to the resources, the users assign to the roles will automatically have access to the resources.
5.Conduct frequent access reviews – Working with role-based access control is not a one-time deal. This still requires auditing and remediation to keep roles in line with changing user needs.
Azure Role-Based Access Control
Azure Role-Based Access Control is the practical implementation of the abstract functionality we’ve discussed so far. It helps administrators manage access to Azure resources and defines exactly what they can do within that resource. Azure RBAC can be view as an authorization system base on Azure Resource Manager (ARM) that helps with granular access management.
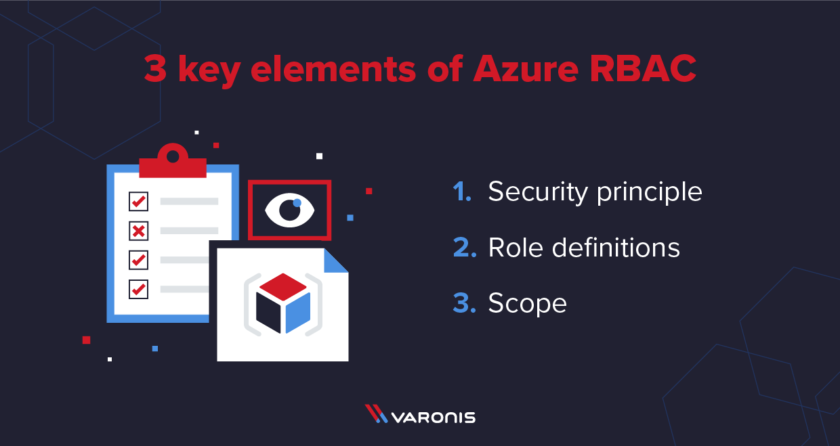
In Here Assignment in azure has three key elements:
1.Security Principal – The security principal represents a user, group, service principal, or managed identity that requests and receives access to a resource.
2.Role definitions – A role has a set of permissions to different Azure resources that are assign to the security principal. It usually defines the actions that can be perform on the resources.
3.Scope: This is usually the resource as well as the level of permissions for one or more roles.
Scope of Azure can be segment into 4 levels. As well as management groups, subscriptions, resource groups, or directly at the resource level. One point to remember is that the scope has a parent-child relationship and the parent’s permissions are inherited by child resources.
Azure includes several built-in roles that are pre-built in Azure for our immediate use. They are base on industry best practices and how Azure resources are systematic. Azure also provides support for creating custom RBAC functions based on your organization’s requirements.
Once the role is create and the roles are scope, role assignment will be perform to provide access to one or more security principles in the scope. If access to the principal needs to be remove, the role assignment is revoke.
Working with Multiple role Assignment in Azure
While some occurrences, you may need to assign multiple roles to a user or group. This is possible with Azure Role-Base Access Control because Azure RBAC is an additive approach, meaning role permissions overlap and the net effective permission is the sum of two different roles assign to one identity.
Let’s try to understand this with an example. If we consider a user as “B” is assign as “Contributor” role at the subscription level. While the same user is assign a Reader role on a storage account. Then the user’s resulting role will be “contributor” as it includes read access to the storage account.
Assigning User Roles using Azure Portal
To assign roles to other identities in Azure, you must have a role with write permissions to the role assignment
Here are some steps to assign roles to an identity from the Azure portal.
1.Scope Identification
2.Select Role
1)Select the Access Control
2)Open role assignments page
3)Choose the appropriate role
3.Select Identity and Assign Role
1)Select the identity to be provided access
2)Add conditions and assign roles
Scope Identification
Choose the resource you want to allow access to. For our lab needs, we will provide subscription level role assignments.
- Open Azure portal
- From the dashboard, click on the Azure subscription
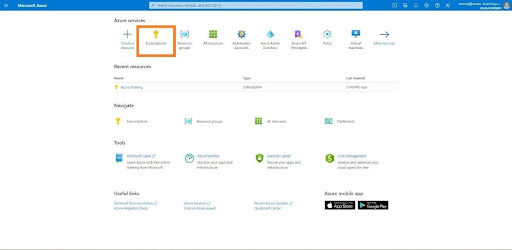
3.Choose your subscription in which you want to assign the for it.

Select Role
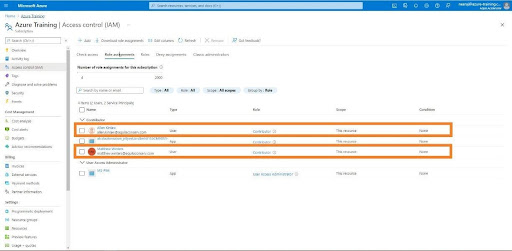
1.Select Access Control (IAM) from the left-hand menu
2.On the Access Control page, click on the ‘Role Assignments’
3.You can use this page to view subscription level role assignments as we are working on subscription level role assignments.
Select the appropriate role
4.Click on the ‘Add’ button and then select the ‘Add role assignment’ option.
5.Here you can give the permissions you want. The purposes of the workshop, you can select the role of collaborator.
You can also use the search box to search for the role by name. Each role displays its description to clarify the purpose.
Select Identity and Assign Role
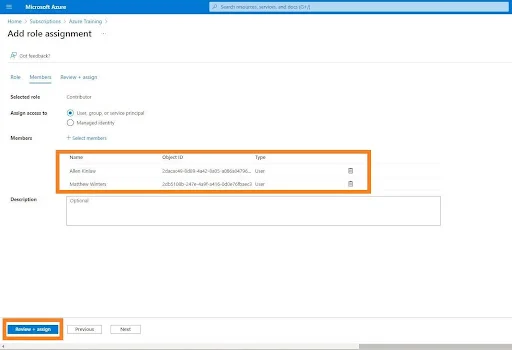
6.After the role has been select, choose the ‘Members’ tab to add members to the role.
8.In the popup that appears, the names of all users will be display, from which you can select one or more users. After selecting the users, click the ‘Select’ button.
9.Chosen users will be displayed on the “Add Role Assignment” page. Then You can then click the “Review and Assign” button at the bottom of the page.
10.In the ‘Review + assign’ button page Click that again.
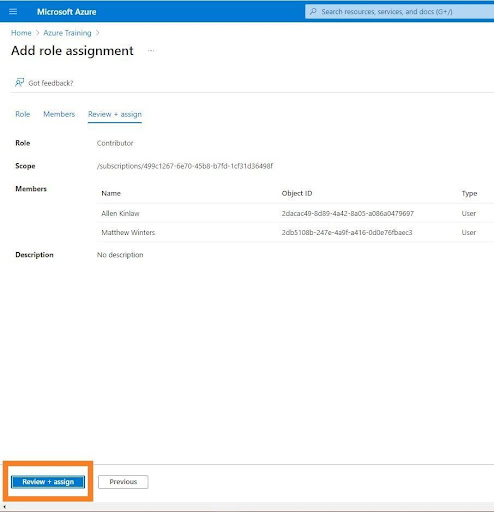
11.It will take a few minutes to display the selected users will be assign the “Contributor” role at the subscription level.
Summery
Role-based access control is a convenient approach to managing the complexities of managing user permissions.
Not only does this minimize the risk of information breaches and data leaks. It also lowers the organization’s overall operating expenses by reducing the manual effort of IT and administrative professionals.
Remember that role-base access control is not a complete security solution that can be use only to replace all other security performs to manage cybersecurity, but should be use in conjunction with other security performances across the organization.


